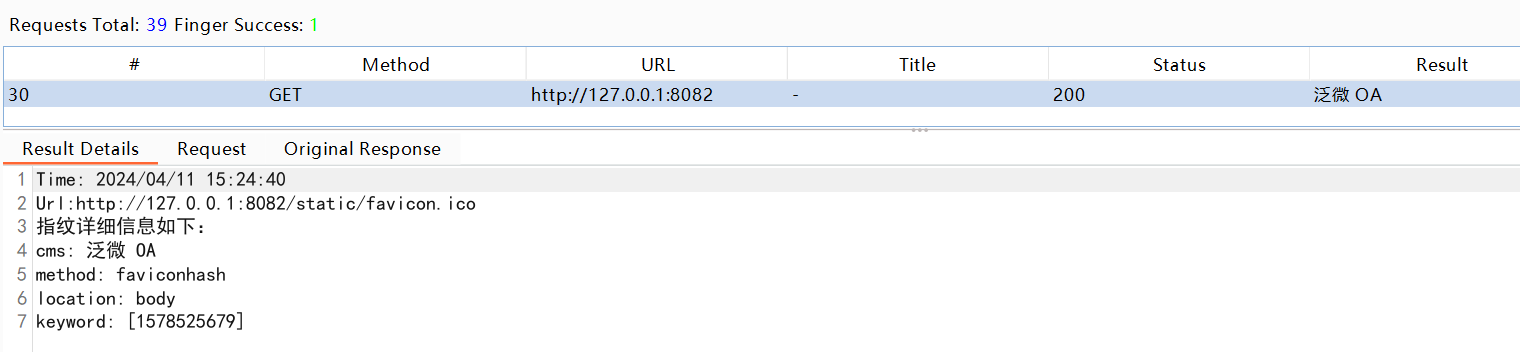
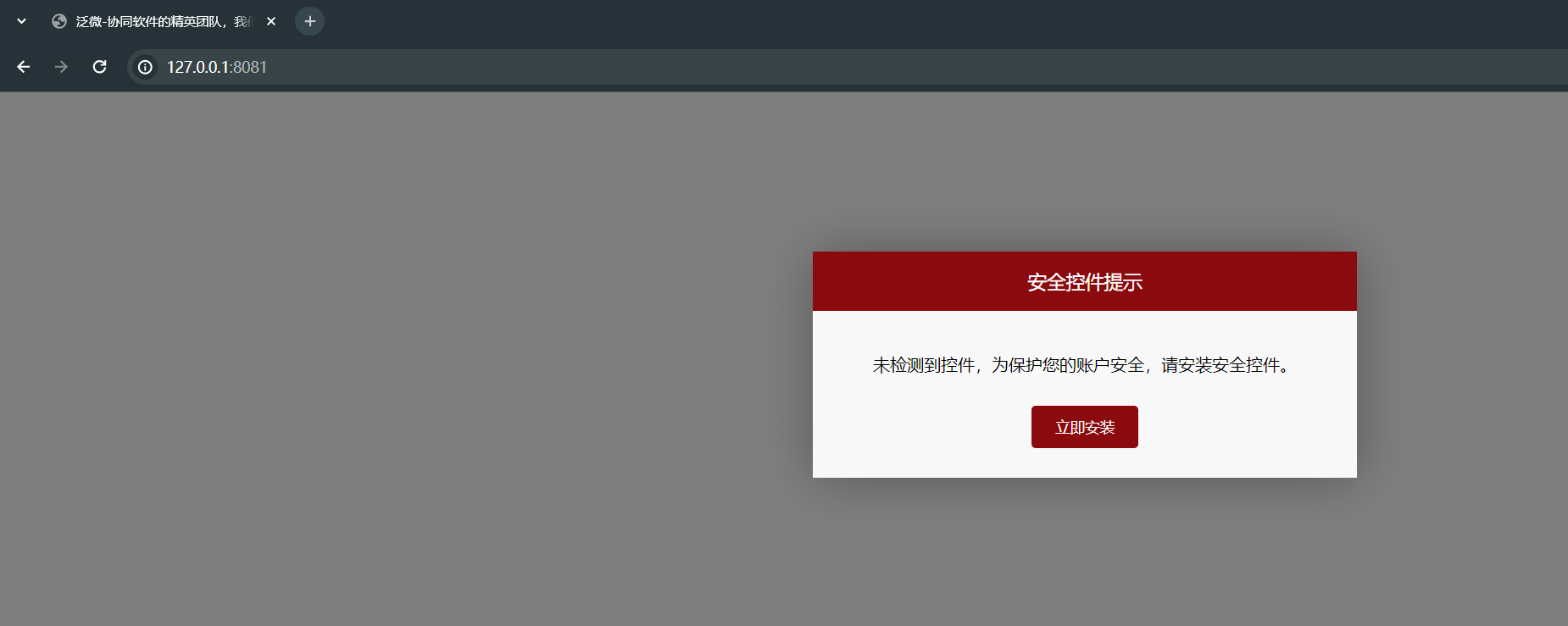
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
| from flask import Flask, send_from_directory, request, make_response
app = Flask(__name__, static_folder='static')
@app.route('/')
def index():
return send_from_directory(app.static_folder, '1.html')
@app.route('/test.exe')
def index1():
return send_from_directory(app.static_folder, 'test.exe')
@app.route('/mobile/ /plugin/browser.jsp', methods=['GET'])
def get_browser_plugin():
# 创建并返回一个HTML响应
response = make_response('', 200)
response.headers.update({
"Server": "WVS",
"Cache-Control": "private",
"X-Frame-Options": "SAMEORIGIN",
"X-XSS-Protection": "1",
"X-UA-Compatible": "IE=8",
"Content-Type": "text/html; charset=UTF-8",
"Connection": "close",
# "Date"和"Content-Length"头通常由服务器自动设置,这里可以不设置或动态生成
})
return response
@app.route('/mobile/ /plugin/browser.jsp', methods=['POST'])
def post_browser_plugin():
if 'isDis' in request.form and 'browserTypeId' in request.form and 'keyword' in request.form:
response_content = '{"operates":[],"prePage":1,"nextPage":1,"browserUrl":"","values":[],"pageSize":10,"hasNext":false,"countSql":"","totalCount":0,"hasPre":false,"isUsed":true,"result":[{"show2":"","show1":"2DE8C18F8A2E60C3B096370AE9812915%","id":1}],"baseSql":"","names":[],"pageNo":1,"autoCount":true,"totalPages":0,"orders":[],"conditions":[],"orderbys":[],"autoGet":true,"first":1}'
response = make_response(response_content, 200)
response.headers.update({
"Server": "WVS",
"Cache-Control": "private",
"X-Frame-Options": "SAMEORIGIN",
"X-XSS-Protection": "1",
"X-UA-Compatible": "IE=8",
"Content-Type": "text/html; charset=UTF-8",
"Connection": "close",
# "Date"和"Content-Length"头通常由服务器自动设置,这里可以不设置或动态生成
})
return response
else:
# 如果缺少任何一个字段,返回200 Bad Request
return make_response('Bad Request', 200)
if __name__ == '__main__':
app.run(host='0.0.0.0', port=8082)
|